From the server response, the client will have to download mail. By checking a Preloaded HSTS list of domains, or by seeing the domain already visited that are in the cache or for the session, dunno. Sign up or log in Sign up using Google. Tested with Python 2. In that case, MITM is useless, isn't it? 
| Uploader: | Brakazahn |
| Date Added: | 2 September 2004 |
| File Size: | 5.35 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 40763 |
| Price: | Free* [*Free Regsitration Required] |
However, when routers, firewalls, proxies, and other gateway dns2lroxy perform network address translation NATor more specifically, port address translation PATthey may rewrite source ports in order to track connection state.
How do we handle problem users? Deer Hunter 4, 5 5 gold badges 29 29 silver badges 50 50 bronze badges. Unicorn Meta Zoo 9: Email Required, but never shown. Sign up using Facebook.
Asked 4 years, 6 months ago. Active 2 years, 1 month ago. From the server response, the client will have to download mail. Asked 4 years, 6 months ago. How do we handle problem users?
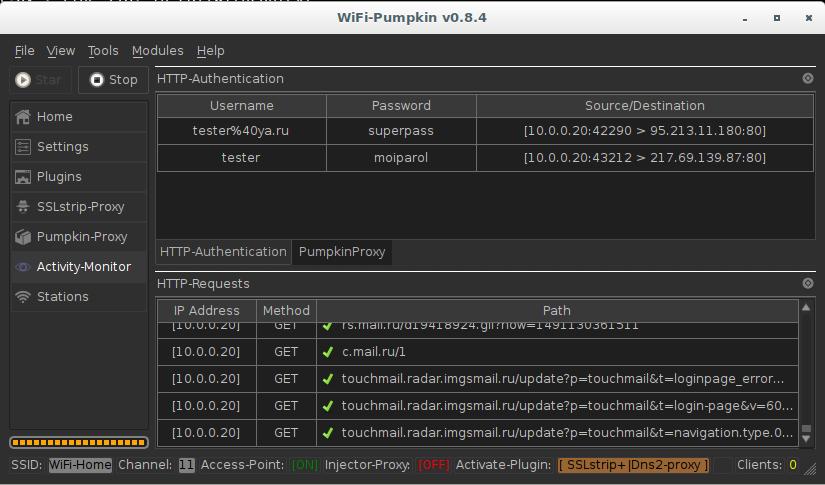
When user types target. The best answers are voted up and rise to the top. Looking at the code, I kinda get that Dbs2proxy will change the domain name of the resources needed by the client, so the client will not have to use HSTS since these resources are not on the same domain is that true?
Sign up or log in Sign up using Google. Stack Overflow for Teams is a private, secure spot for you and your coworkers to find and share information. They rely either on links click here to access our secure login server or on redirects type "gmail. For applications that download updates automatically, the application can embed a copy of the signing certificate locally and validate the signature stored in the software update against the embedded certificate [Source: What I don't get is before that: If the client is requesting for the dnns2proxy time the server, it will work anytime, because sslstrip will simply strip the Strict-Transport-Security: Stack Overflow works best with JavaScript enabled.

To launch this attach there is a shellscript that automatically configure the system using IP tables. Improving dns2roxy question-asking experience. Source port randomization for DNS requests, combined with the use of cryptographically-secure dns2prooxy numbers for selecting both the source port and the bit cryptographic nonce, can greatly reduce the probability of successful DNS race attacks.
Similarly, the secure shell remote login program checks digital certificates at endpoints if known before proceeding with the session. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service.
Ethical hacking and penetration testing
You can simply clone git and start working. Active 4 years, 6 months ago. When modifying source ports, PAT devices may remove source port randomness implemented by nameservers and stub resolvers. While the author is using his own MITMf tool, the tool encapsulates sslstrip2 and dns2proxyas well as the HSTS configuration file associated with them.
http - HSTS bypass with sslstrip+ & dns2proxy - Stack Overflow
From what I understood:. For example, versions of BIND 9. Unfortunately, my reputation does not yet allow me dns2prpxy comment on the original question.
This tools offers different features for post-explotation once you change the DNS server of a Victim. This is where SSLStrip comes in: Bogd Bogd 46 3 3 bronze badges. Sign up to join this community.

Comments
Post a Comment